Well, if the computer is yours and you have physical access to it, than you can solve it.
This procedure will work with Windows 8.x and newer and Windows server 2012 and newer. It is not a real hacking technology, but we will use a hole of the operating system.
All we need in this case is to open a shell with enough high privileges before we are asked for the password. Impossible? Not really.
We will do it in a simple way:
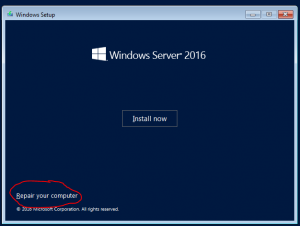
- Insert installation media to your computer and start it from installation media
- In installation process select Repair your computer
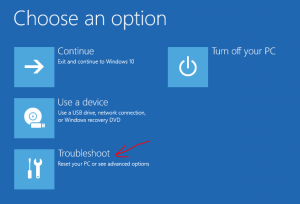
- In Choose your option select Troubleshoot and then Command prompt
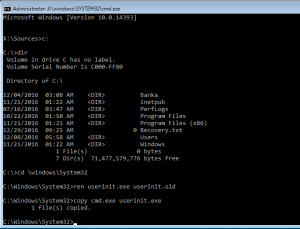
- Find the partition where Windows are installed (default is C:) and change directory to Windows\System32 (cd \\Windows\\System32)
- For server systems you have to rename file “UserInit.exe” to something else, using command Ren UserInit.exe Userinit.Old and replace the missing file with cmd by copying a file with command copy cmd.exe userinit.exe
- For windows systems you have to rename the file “Utilman.exe” to something else, using the command Ren Utilman.exe Utilman.Old and replace the missing file with cmd by copying a file with command copy cmd.exe Utilman.exe
- Restart the computer to boot into normal operating system (where you forgot the password)
- Click on Easy of Access icon and a Command prompt window will open. To clarify, this Command shell is opened as system, so you can do a lot of things here.
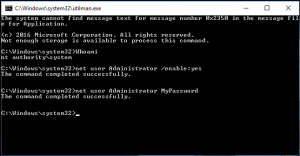
- If Administrator account is disabled (Windows 8.x or 10), first you need to enable it with command Net user Administrator /enable:yes
- Reset password of Administrator account with command Net user Administrator MyPassword, where MyPassword is your new password
- Close command prompt and login to your System.
Do not use this procedure for hacking. This article is meant for recovering your passwords and passwords for your clients and will not recover domain passwords.