Windows server 2016 TP5 is available and there are few new features to try. Personally I was happy to see few new features because they solved some problems to me.
The first feature that I like is Session-based desktops. Practically is a new approach to VDI –we can say that is hybrid deployment between VDI and RD Session host. The result of this deployment will be that any user will have dedicated server to connect – one deployed server is full desktop for one user. This kind of deployment with installed desktop experience will look as Windows 10 and can replace deployment of Windows 10 based VDI. So where is difference? Easy to say. You can use this type of deployment in SPLA environment where VDI scenarios are not allowed, you can use it in Microsoft Azure (here you cannot deploy VDI as you cannot access to host) and similar scenarios. There is also a licensing advantage as you not need Windows 10 licenses and VLS – you can license all instances of “VDI machines” using one Windows server 2016 Datacenter license. This is cheaper!
The second feature I like is SQL database location for RD gateway. Now you can locate this database to Azure. My opinion is that in some cases this will be very positive and the right solution when we talk about hybrid deployments. It just open new possibilities to deploy a RDS farm.
You can read more about what’s new in RDS 2016 here.
Category: Windows Server
Free Microsoft E-Books
Need to learn about Microsoft technologies? If the answer is yes, you can start downloading E-Books from here. They are completely free and very useful.
Try them!
Make your Local Admin account more secure
It is about a year from when Microsoft released LAPS (Local Administrator Password Solution). This is a great tool for keeping your local admins under control and secure.
As we know, a lot of local accounts have weak passwords and we don’t care about this. This’s dangerous! Even if you have a weak local admin password, you can still break a PC with him. If you have the same password for local admins in entire environment, you can have a problem when someone knows this password… Thinking in this way, we have a lot of reasons why to use LAPS. And it is simple to install and use it; it is true that will extend AD schema, but don’t care about this – it is not critical.
LAPS is downloadable from here and it is FREE. Here is also nice post how to install and configure it and this is all you need.
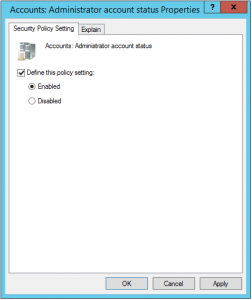
The only problem that I had is enabling and renaming local admin account true GPO, but here is also a very easy trick:
When I install client operating system thru MDT or System Center, I always disable admin account in the last step. It is more secure, but you can have problems if something goes wrong with computer relationship in domain. If you have the same situation, you have to enable Account in Group policy setting Computer Configuration > Polices > Windows Settings > Security Settings > Local Polices > Security Options by enabling setting Accounts: Administrator Account Status. After doing this, it is suggested also to rename Administrator account. This could be done in the same place with setting Account: Rename Administrator account or thru Group policy preferences.
Using FSRM against Ransomware
Are there positive and negative sides? Of course they are, the most important negative thing I recognize is that we are using technology based on file type. Actually we are trying to prevent to write all known file extensions that can be written on our system. This will work if we know the extension and we have to search for new used file extensions and add them as blocked file types. But there are also positive things: we don’t need to buy anything, we have all we need ready on our server – we have just to use it! It is very simple to configure and maintain and it works!
When I read this article, I was surprised why I have to do all those steps thru GUI? We can simply use PowerShell that is quicker and it will do exactly the same things every time we will start it. Well, I made a script that you can run on every server you have to protect and for every share or partition you want to protect. There is only one think that you cannot protect: system drive if you try to prevent whole drive. In this case, the protection will be passive and not active and there is no way to change it (but I hope that you don’t share system drive).
Things that you have to know are basic, just few data:
- Path to protect
- SMTP server for sending mail (and be careful with authentication! Test it!)
- Mail address form which mail will be sent
- Mail address from administrator
- Script that you want to run after detection (if you want)
To prevent malware, you can use an additional build in function: AppLocker and also this is explained here. And by the way, the approach is tested on Server 2016 TP5 – it’s working!
Kaspersky cause Hyper-V error 0x80070005 when creating switch
 As I trust and use Kaspersky Antivirus, I had some problems in last month or two. It seems that Kaspersky is not really well integrated with Windows 10 and you have to expect some problems.
As I trust and use Kaspersky Antivirus, I had some problems in last month or two. It seems that Kaspersky is not really well integrated with Windows 10 and you have to expect some problems.
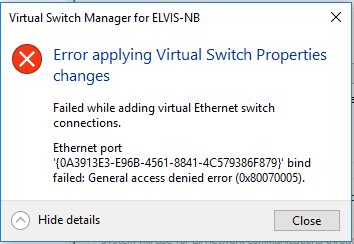
In my case, I use Kaspersky Small Office Security and this software prevents me to do a lot of actions. I found the issue when I tried to create External Network Switch in Hyper-V console – the problem is when you create a new network adapter. In this case I received an Error Access Denied – 0x80070005.
I received the same Error also when I tried to install Shrew Soft VPN Client. I was always unable to install network component due to Access Deny. Analyzing the problem, I found that there is a problem accessing to folder INF (Change) and some other system folders, but all permissions were as they should be and there was no way to establish the right permissions to get installers work.
Well, removing Kaspersky I was able to solve the problem. But be careful, just disabling the antivirus will not be enough; you have to completely uninstall the entire antivirus and reboot the computer to correct the issue.
Hope that Kaspersky will correct the issue soon. It is my preferred antivirus program and I like it, but unfortunately it is not well integrated with Windows 10.