Many administrators in small environments (where we have Essentials server) have to buy a trusted certificates to make RWW working. The common problem of all those environments is, that there is no money for buying certificates or owners don’t understand why they need to buy certificates. This is why I am writing a post how to certify RWW with Let’s encrypt certificates.
It is a bit different to do it because Let’s encrypt certificates have validation period only three months and maybe it seems, you will have a lot of work – but don’t be afraid; we have two ways to simplify this procedure and my preferred procedure is with a product called Certify.
- First download Certify from this link (https://certify.webprofusion.com/).
- Install Certify with default options as you can see on screen shots. There is no need to change any settings; the application is simple and can be always installed with default options.
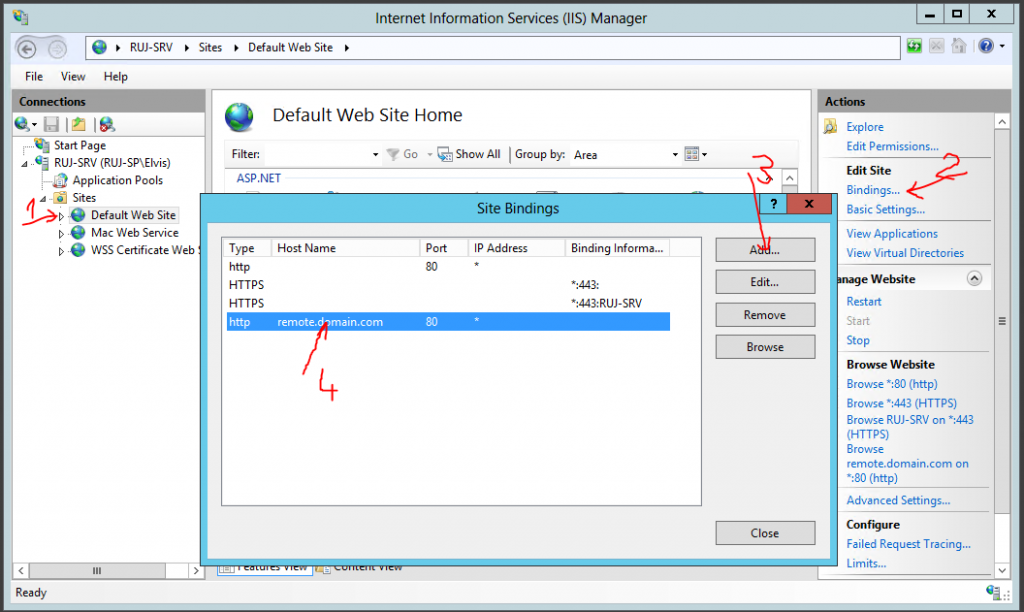
- Now you have to modify Essentials server configuration. Certify can issue the certificate banded to name of default web site in IIS. This means that we have to modify default site bindings (look at picture) in a way that we have public RWW name bind to default web site and port 80 – 443 SSL is not needed.
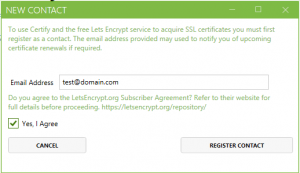
- For the first time, when you enter Certify, you will need to add your contact details. It is just to care about your certificates.
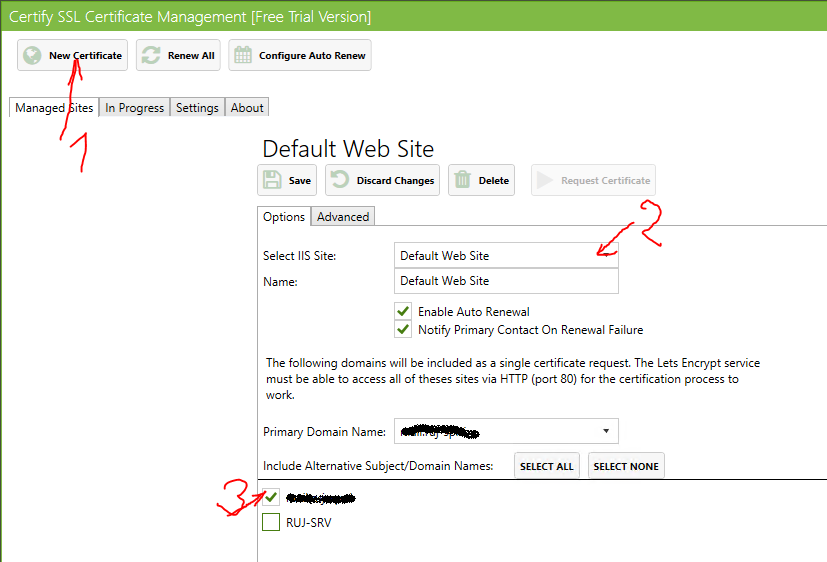
- Open Certify and start registering the new certificate.
- From the form select default web site and clear checkbox from local server name.
- CLick Save.
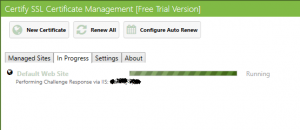
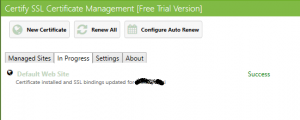
- Click Request certificate. At this point you will receive the certificate – be careful on firewall rules; you need to open port 80 and 443.
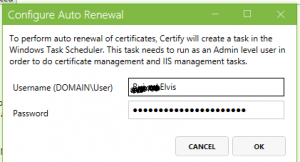
- We have now to do the last step: go to Configure Auto Renew and type Username and Password for user who is able to request the certificate.
That’s all you need. Now you have configured RWW with free trusted certificate, the certificate will be renewed automatically when will expire and you don’t need to manually renew it anymore.
The same process can be done on any IIS website or for any certificate that could be requested thru IIS.